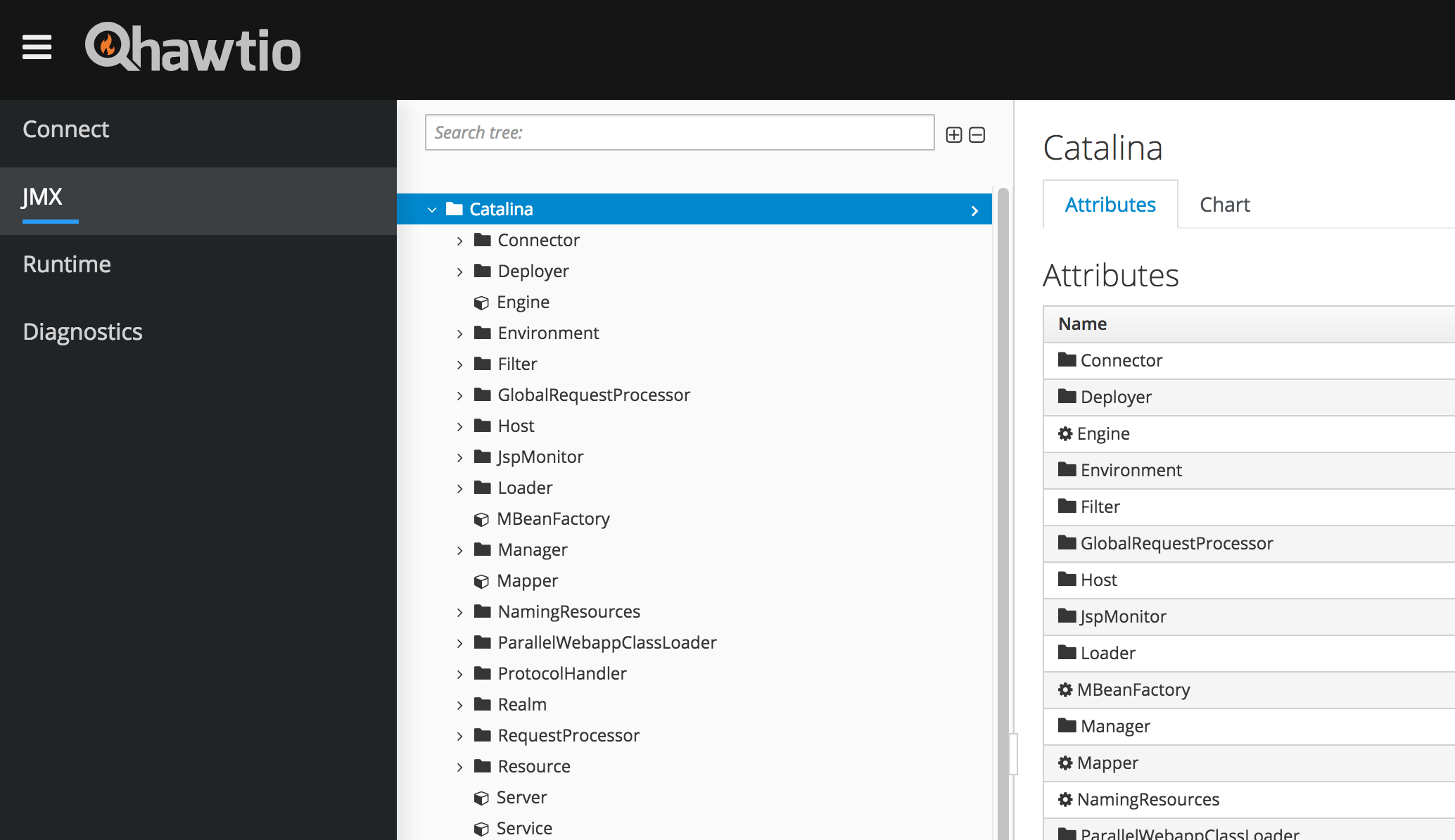
JMX Monitoring Then and Now - SRE Tools
Evolution of JMX monitoring Monitoring is an essential part of Site Reliability Engineering and Infrastructure Services. I have started my career a decade ago when there was no many JMX monitoring tools and APMs(Application Performance Monitoring) available. I have...

Terraform google_compute_instance Example - with Remote Exec
In this article, we are going to see how to create a Linux Virtual machine and provision it using the Terraform remote execution strategy. We are going to be using SSH method to connect to the Virtual machine and provision it on the go by executing some startup Shell...

Ansible Copy file or Directory - Local to Remote | Devops Junction
In this article, we are going to see how to copy or SCP files and directories from local to remote. Control machine to the remote server. We are going to learn how to SCP files from local to the remote host Ansible has dedicated modules to support the copy between...

Weblogic Datasource Creation WLST script & Ansible Playbook
In this post, we are going to see how to create a weblogic data source using WLST script and an Ansible Playbook. For this example, we are going to create a simple generic data source. What is DataSource? Quick intro A Datasource or Connection Pool is simply a...
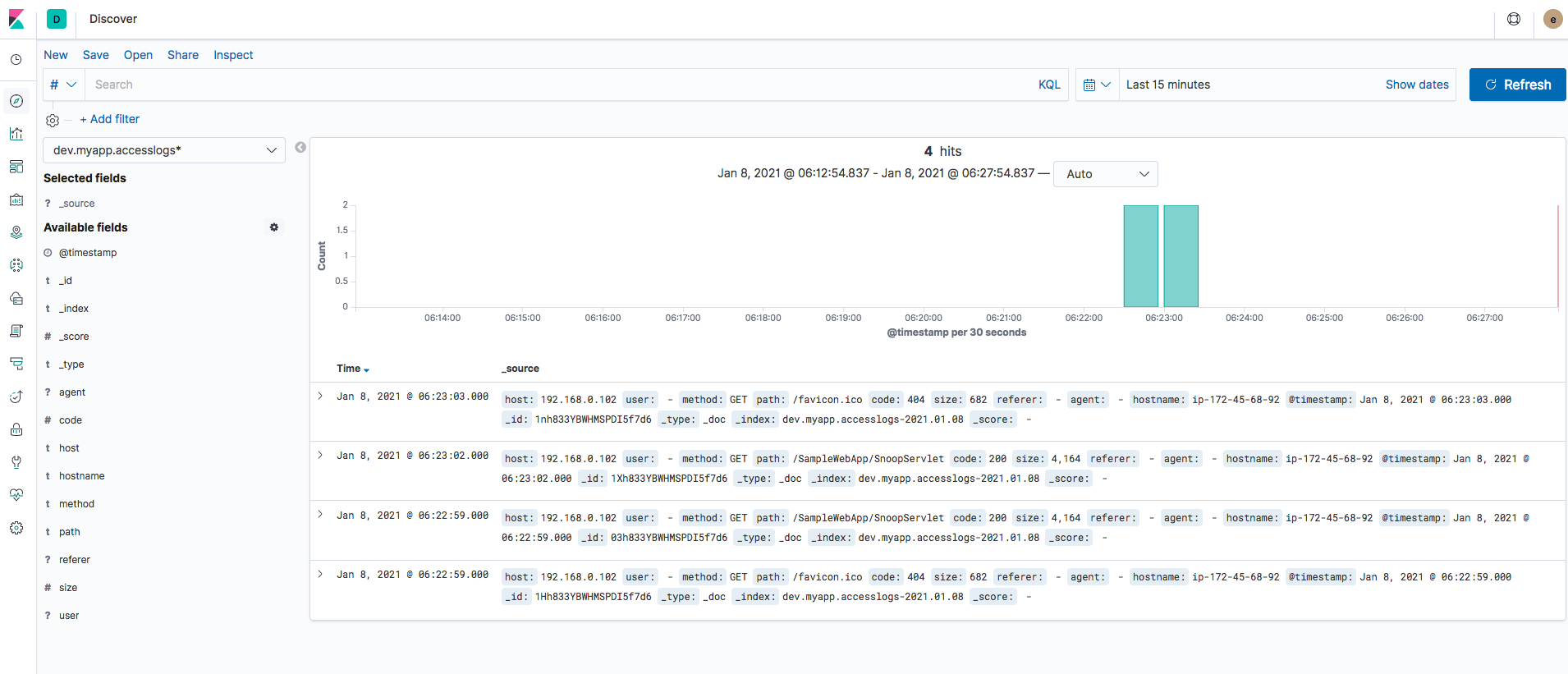
FluentD Tomcat Elastic Search Example - EFK
In this article, we are going to see, How to collect tomcat logs with FluentD and send to Elastic Search. FluentD Tomcat Elastic Search (EFK) setup would be covered in detail. Technically this is known as EFK stack. an efficient and better alternative for the ELK...
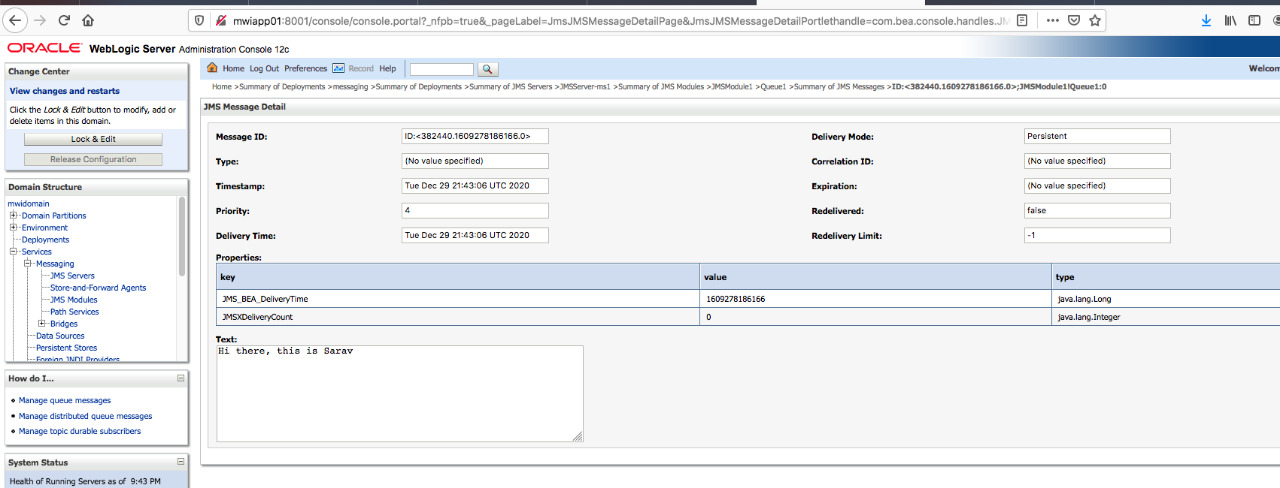
Weblogic JMS Queue Creation WLST script and Ansible Playbook
In this post, we are going to share a WLST jython script and an ansible playbook to create JMS Queues in weblogic 12c Here is the simple jython/python WLST script. The script is simply designed to create and set up a fully functioning JMS Queue in weblogic. It creates...
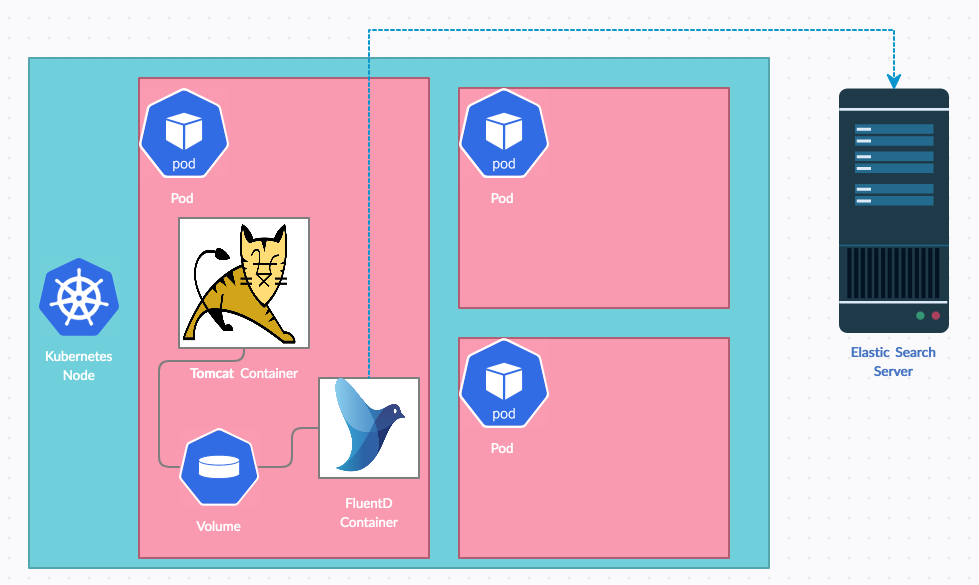
Kubernetes Sidecar - Logging with FluentD to EFK
Introduction Log management in Infrastructure has changed tremendously in recent few years and we are a having wonderful products in the market to manage, parse, analyze log files These tools are being used extensively for incident management, alerting, security...
CPU and Memory consuming Java WebApp - For testing
There might be times where we might wonder what process is consuming all the system memory or CPU. We invest a lot of time debugging it and looking at the JMX graphs and then we finally find a bug in the code and fix it for good. On the other hand, there are times...

Automated Oracle Database Backup to S3
The Beautiful thing about Digital world is that we have a Ctrl+z button, snapshots and backups to go back in time and correct our mistakes, which is not possible in our real life. Enough with a philosophy. I would not have to tell you how crucial backups are and when...

How to get or set UNDO_RETENTION parameter - Oracle
I have recently encountered an issue while trying to export the Oracle DB using the expdp command and my database size was huge, therefore I got an error stating that Snapshot is too old When I researched further I noticed that my UNDO_RETENTION was too less and set...
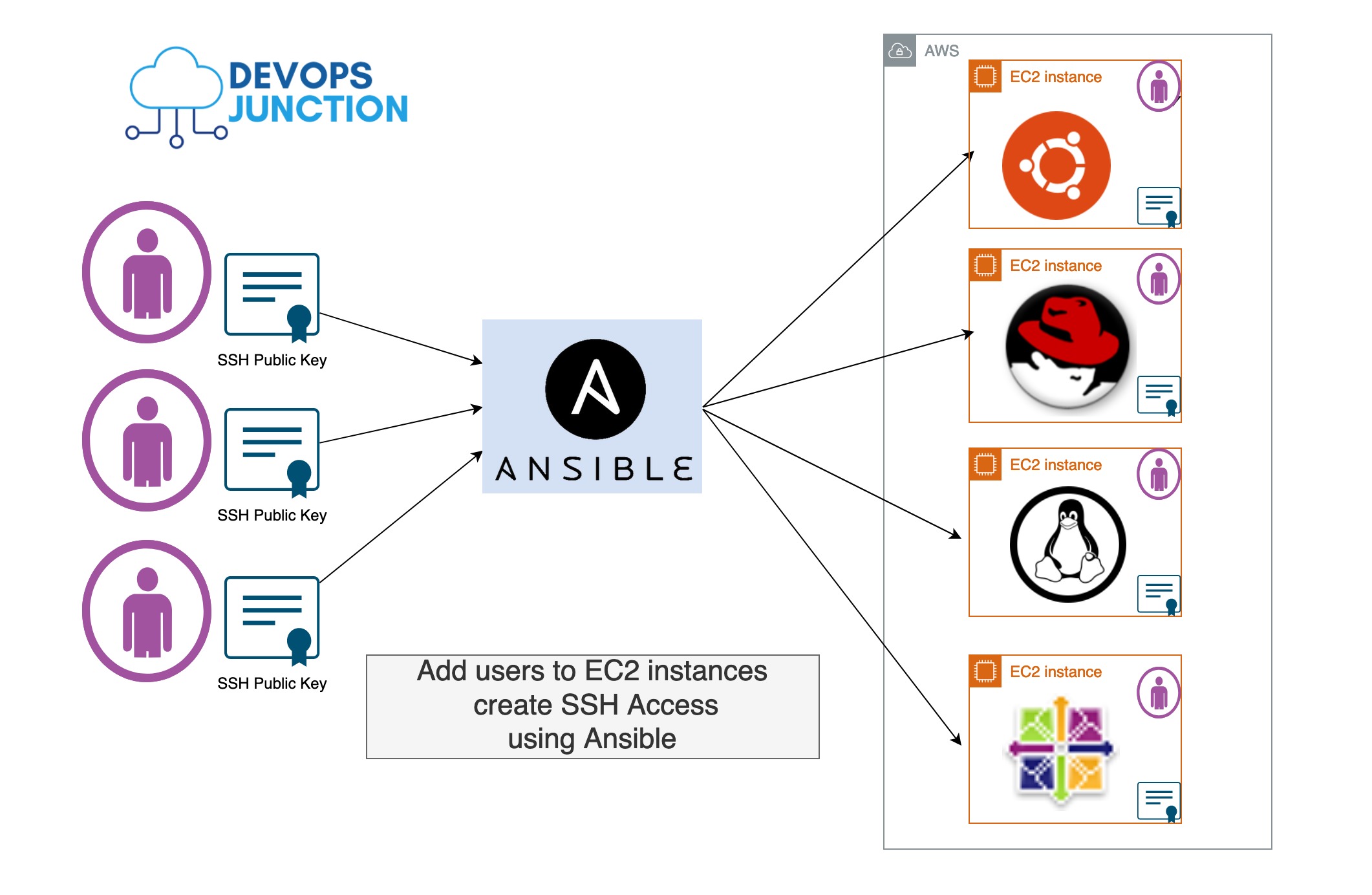
Add users to EC2 instances with SSH Access - Ansible
The objective of this article is to talk about how to add new users to EC2 instances and copy their SSH Keys to grant them SSH access. Consider yourself managing an AWS Infra with 100+ EC2 instances and you have a new hire in your team who should have his SSH access...
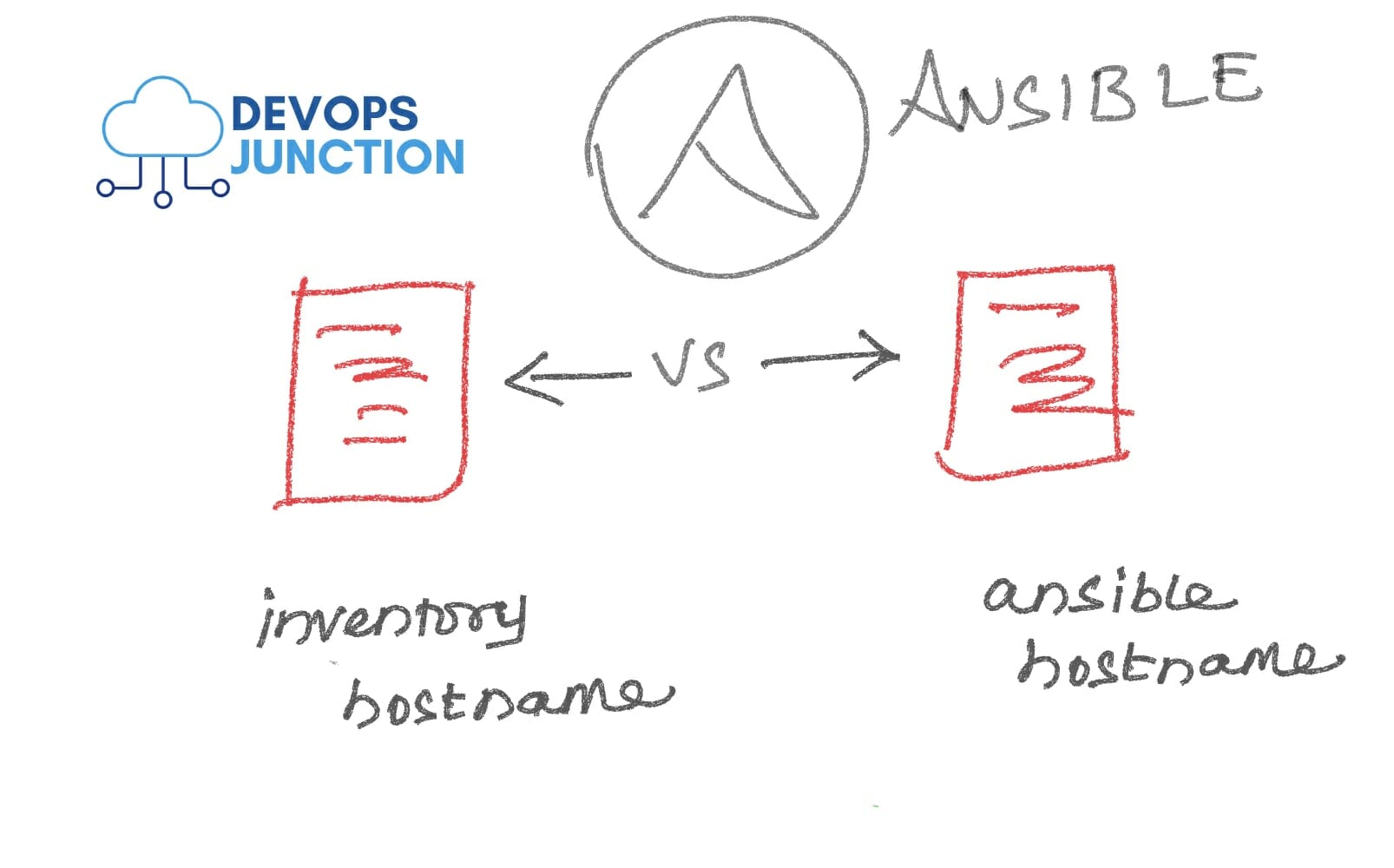
Ansible Inventory_hostname & ansible_hostname Examples
In this post, we are going to see two built-in variables of ansible mostly used in Ansible playbooks and they are inventory_hostname and ansible_hostname while both these variables are to give you the hostname of the machine. they differ in a way, where it comes from....
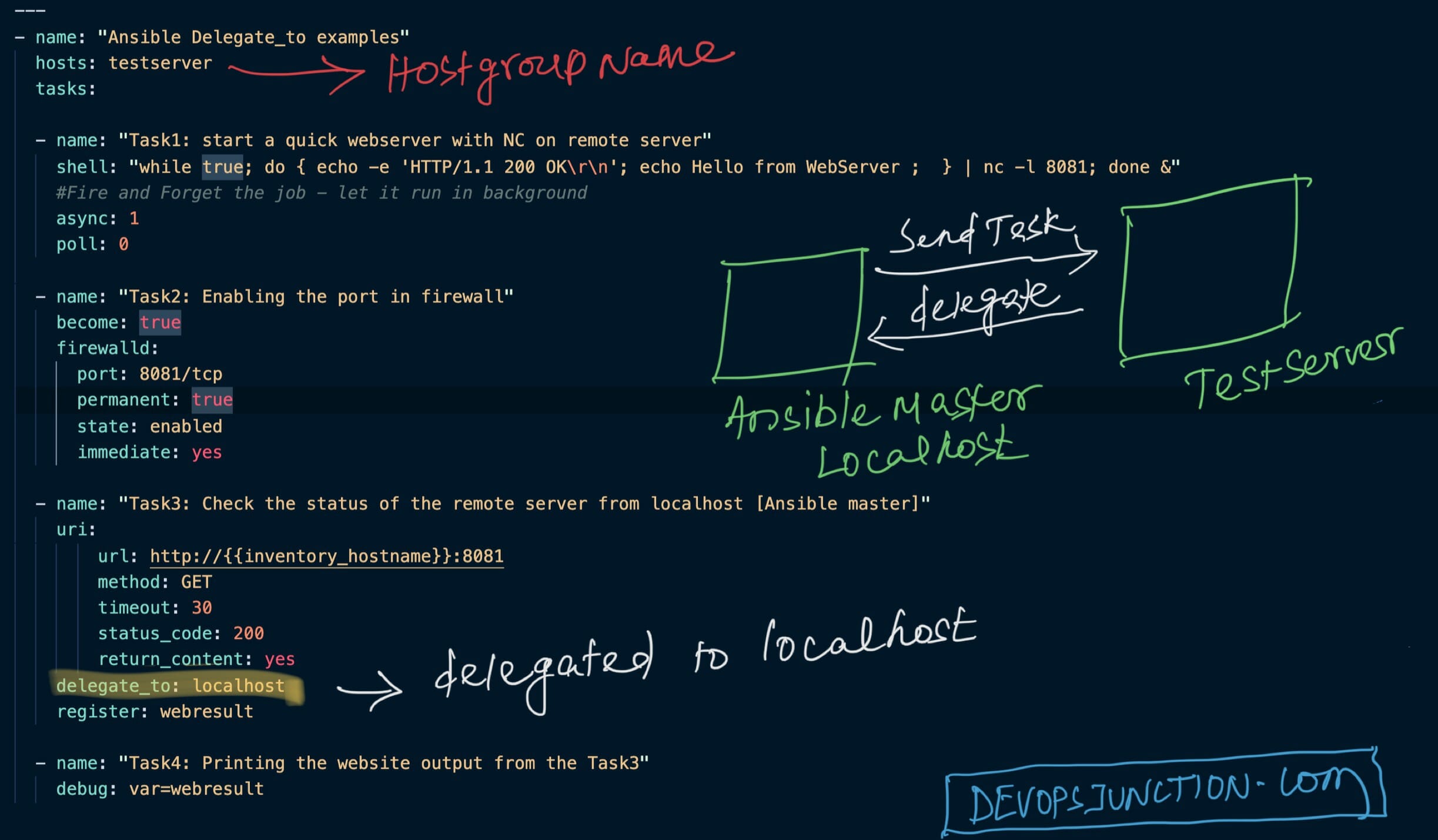
Ansible delegate_to Examples - Run task on specific host
Ansible Delegate_to module helps us to execute a specific task in our playbook to run in other host or machine. This process of handing over the control of execution to another host (or) executing a task in another machine is called as delegation and the module...
How to decrypt HTTPS traffic using SSL Proxy
Introduction to a historical problem Are you a Developer, DevOps Engineer, Infrastructure Engineer, Middleware admin then you might have had this question at least once in your career? How to see what is being transmitted between the Server to Server [or] Client to...

How to Deploy Tomcat on Kubernetes Step by Step
Overview In this post, we are going to see how to deploy tomcat on Kubernetes. How to Deploy Tomcat based web application into Kubernetes. We are taking Google Cloud - Kubernetes Engine (GKE) for our example and creating our Kubernetes Cluster with 3 nodes You can do...
Articles for DevOps Beginner
No Results Found
The page you requested could not be found. Try refining your search, or use the navigation above to locate the post.

