
F5 LTM irule to mark cookie as secure and httponly and Why
Some Background When it comes to handling the web application related vulnerabilities. Most of the vulnerabilities could be fixed by having the proper configuration at the F5 level. By using the right configuration at the F5. like having proper SSL Cipher at the SSL...
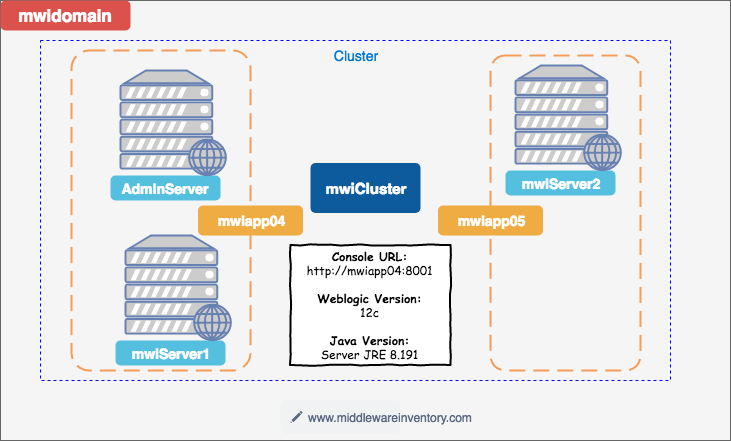
Ansible Role to install and build weblogic 12c with Clustering
The Objective We are going to create an Ansible role (or) playbook to quickly build a distributed, multi-node, Fully featured Weblogic Domain with two managed servers and a horizontal cluster and machines In a single line, Ansible role to build, Weblogic...

Ansible When Variable is defined or undefined Examples
The Purpose The purpose of this post is to give you a real-time example and explanation of how ansible variable is defined and not defined (undefined) conditionals are working along with "when" conditional statement and how it controls the flow of the task and the...

Docker Weblogic : Run Oracle Weblogic 12c on Docker
The Introduction to Docker Weblogic In this post, we are going to be exploring the quick and easy option available to get started with weblogic and Docker. In this post, we are going to see how to create a weblogic container in docker in a few easy steps. The post's...

Weblogic developer vs generic distribution - What is the Difference
Some Background Weblogic distribution is the terminology that depicts the form or the nature of the Oracle Weblogic Installer (or) the installable files. Oracle weblogic 12c can be downloaded in two forms. Generic Distribution Developer Distribution What is Generic...
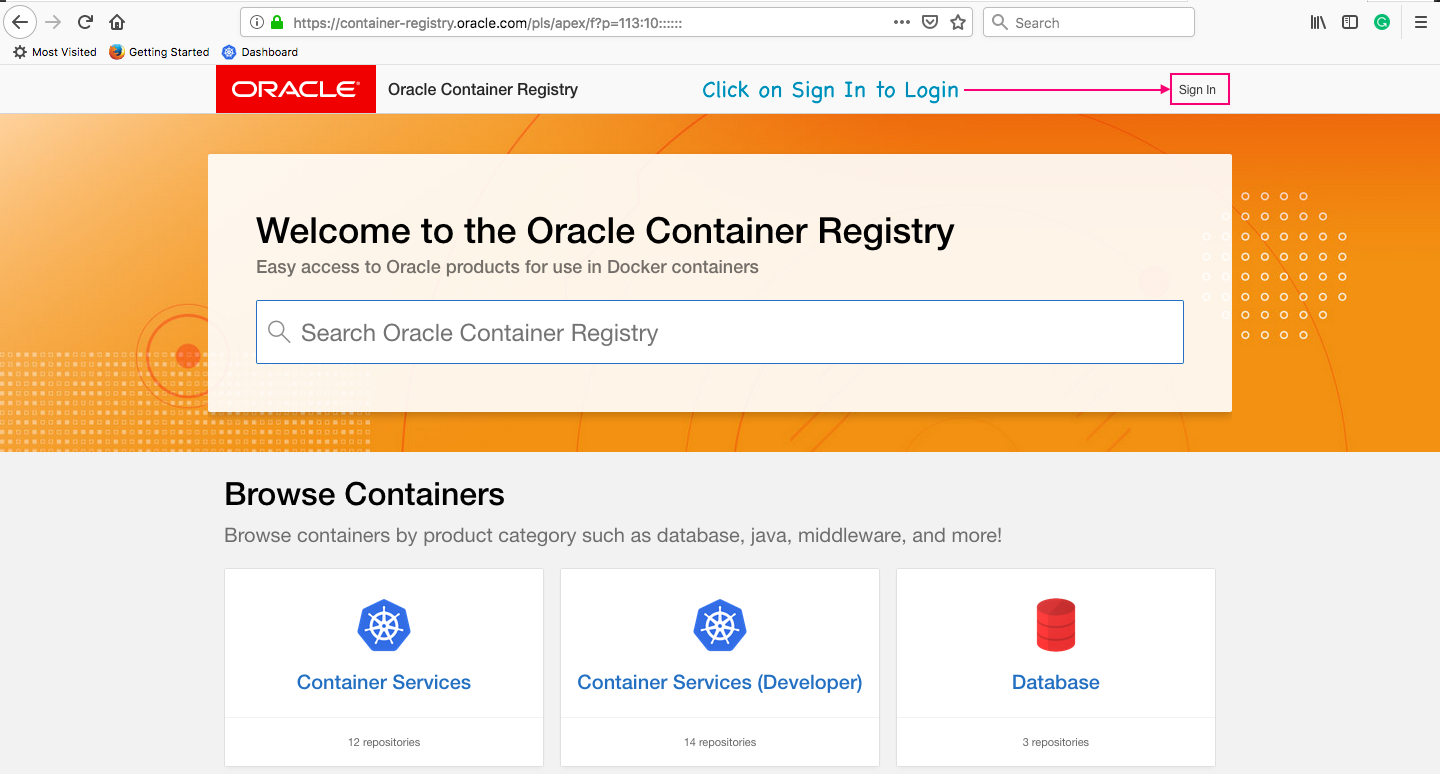
docker pull container-registry.oracle.com - access denied (or) Unauthorized
In this article we are going to see how to fix the access denied and unauthorized errors while using the containers of container-registry.oracle.com. Most of us at times might have got this exceptions access denied and unauthorized while downloading the image using...
How to Deploy docker image to Kubernetes
In this post, we are going to see the Steps to create a Docker Image and Deploy to Kubernetes in 8 easy steps. This post is about the title of this post which is "How to Deploy docker image to kubernetes" For this post, we have used minikube cluster and taken a Mac...
How to find High CPU Consuming Threads - Java Thread Top
The Objective Let it be any Application Server you use such as Weblogic, Websphere, Tomcat, Jboss, Glassfish. (or) Let it be any Java framework or architecture your web application is developed in like Spring MVC, EJB, JSF, DAO. When it comes to administrating the...
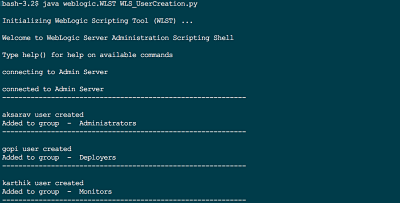
Weblogic User Creation Script WLST
The Objective The purpose of this post to share the WLST script which helps in creating a new user in weblogic 11g or 12c and map them to righteous Group for privileges. Like Administrators, Deployers, Monitors etc. Version Compatibility Weblogic 12c (or) 11g...
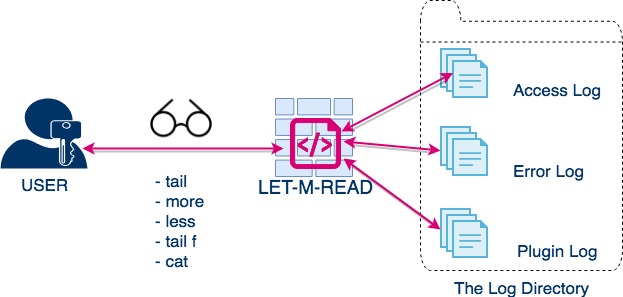
LET-M-READ - Controlled Read Access to Linux Users
An Open Source tool to grant controlled read access to unprivileged users on UNIX based OS to read log files or config files etc. With LET-M-READ system admins can give read access to unprivileged or Guest users. without changing the file permissions (or) directory...

Ansible changed_when and failed_when examples
In this post, we are going to see how to use conditional statements of Ansible such as when, changed_when, failed_when and where to use them appropriately and how it works. By these conditional modules, Ansible provides a way for us to define when should ansible run a...
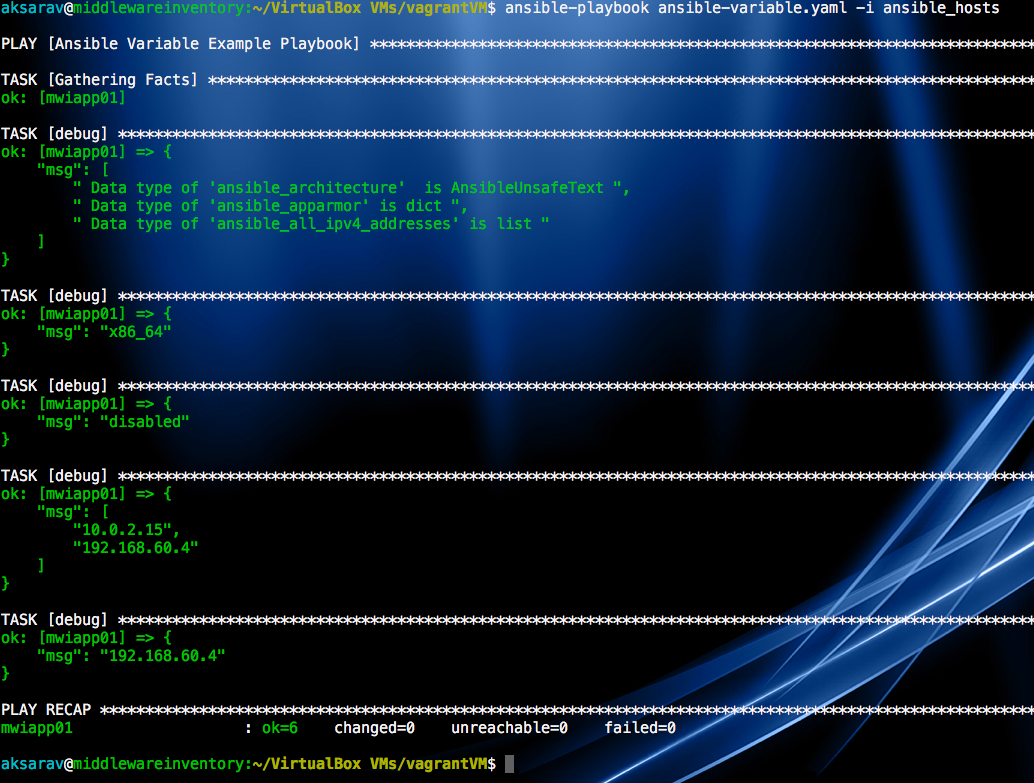
Ansible Facts and How to use them - Ansible Variable list
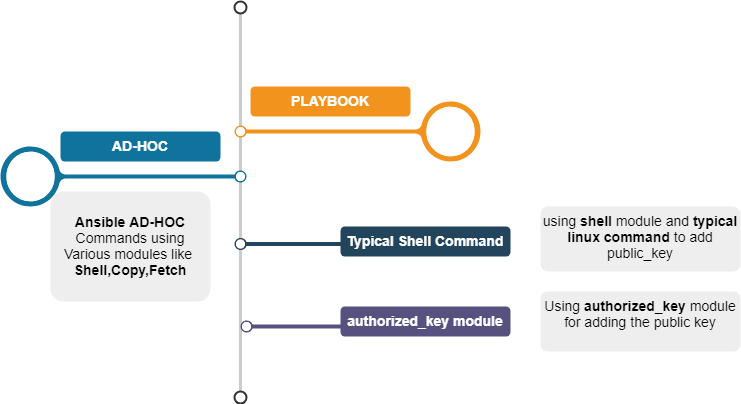
Ansible SSH Key transfer from one host to another - local and remote
SSH Key-based authentication setup in LINUX (or) UNIX based OS is one of the major platform services related task and most frequently executed task by Unix admins. Ansible, An IT Automation tool could automate this tedious task as well. SSH Key based authentication is...
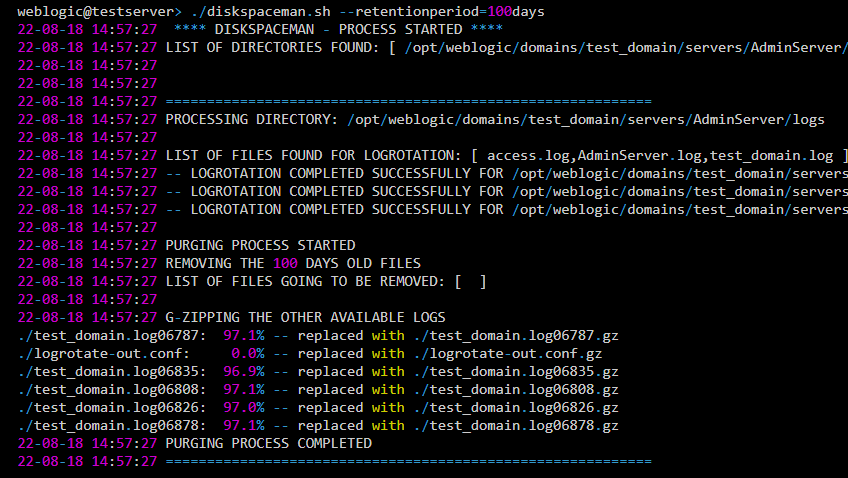
Log Rotation, Purging, Archiving of Application Server Logs - Script
Overview An Automation script Linux for Log rotation, LogPurging and Compressing For weblogic and tomcat Installations. In Big infrastructure when you are running multiple Tomcat, weblogic, JBoss (or) Websphere instances or domains. The Biggest problem that you would...
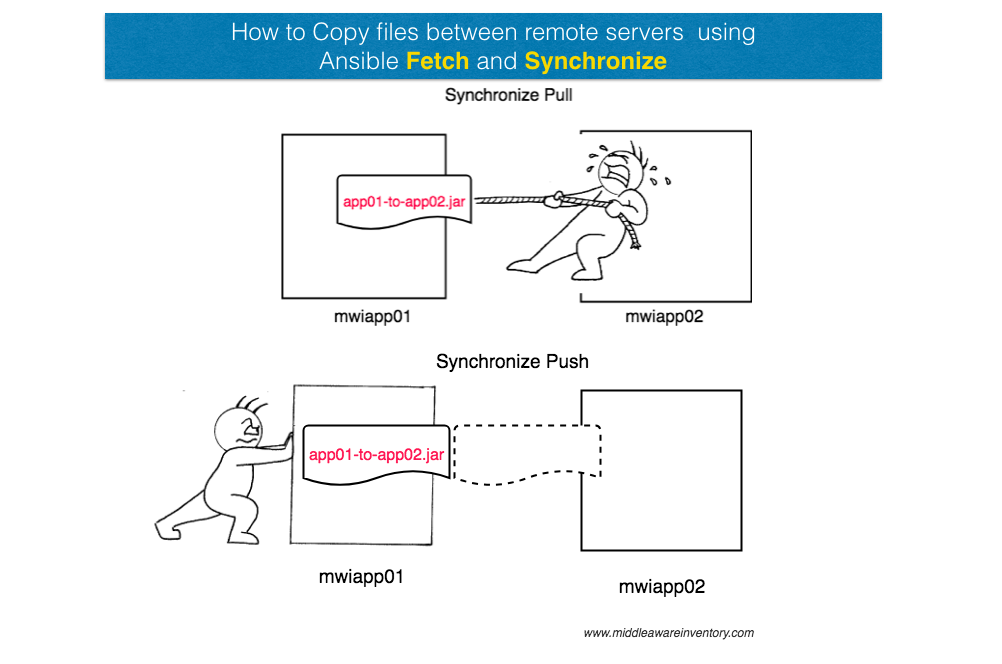
How to Copy files between remote hosts in ansible
How to copy files between remote servers in Ansible ?. is the purpose behind this article. Every article I went and read was giving me suggestions but nothing practical. I simply wanted to do make ansible rsync. I wanted to execute rsync between remote hosts and copy...
Articles for DevOps Beginner
No Results Found
The page you requested could not be found. Try refining your search, or use the navigation above to locate the post.

