
Ansible EC2 Example - Create EC2 instance with Ansible
Infrastructure as Code is getting all attention it deserves and everyone is trying to find their way to the `Completely automated Infrastructure Provisioning & Management` While there are a lot of tools available now in the market starting from Terraform, AWS...

Ansible Async Poll Examples - Ansible nohup, task in background
Not all the tasks we run in our playbook are short and sweet. Some of them would take a long time but we cannot afford to sit tight and watch the screen. We got better things to do. Some of the long-running tasks could be Downloading a Big File from URL Running a...
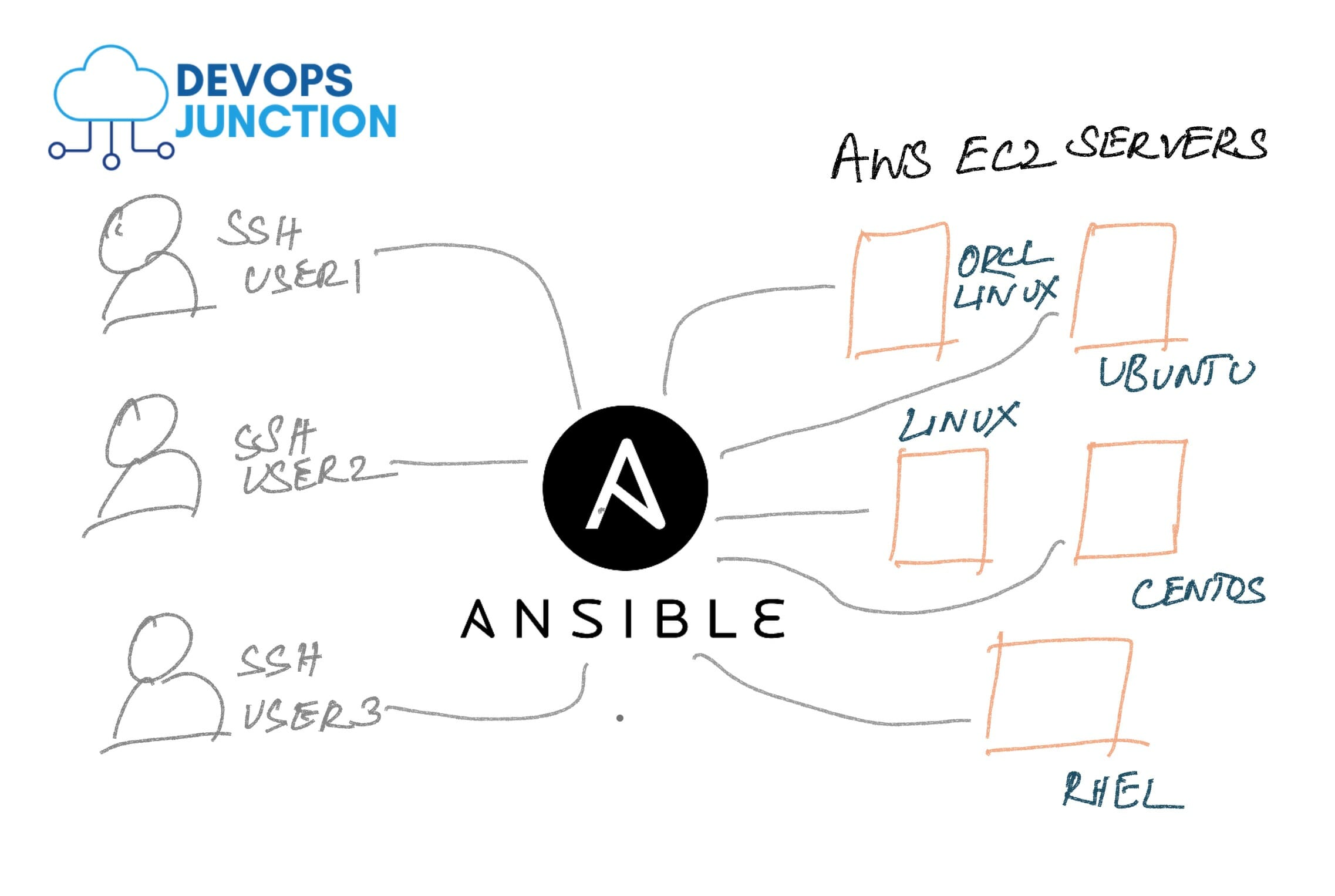
Add SSH Key to EC2 instances with Ansible - Automated
Whether it is On-Prem (or) Cloud-hosted, A Typical Non-Containerized Enterprise infrastructure would have ample of Virtual Machines aka Servers [ Linux ] Let us suppose that you work for the DevOps team of a Big Organization where you manage 100+ ec2 instances. You...

Hide Server Banner and Product Info from HTTP Header
Overview Probably one of the first tasks to do while setting up the production environment is to mask the Apache (or) IHS (IBM HTTP Server) version and Server Banner in a header. This is not critical but considered low risk as information leakage vulnerability and...

Apache ClickJacking Attack - How to Fix
What is Apache Clickjacking Attack and How to Fix Clickjacking is a well-known web application vulnerabilities. For example, it was used as an attack on Twitter. To defence Clickjacking attack on your Apache HTTPD web server, you can use X-FRAME-OPTIONS to avoid your...
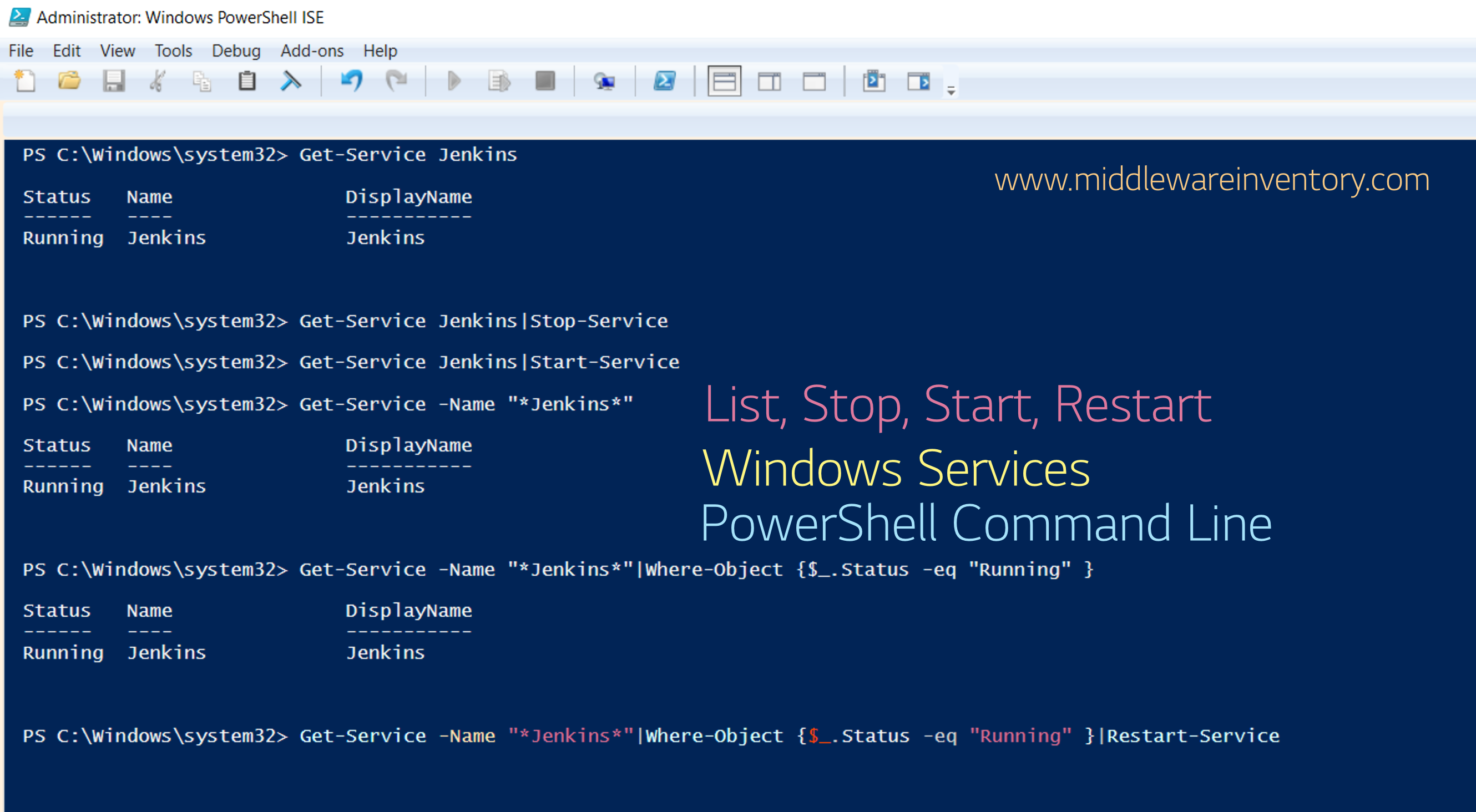
Stop, Start, Restart Windows Service Command Line - How to
Windows Service management through the command line is really a good approach when you want to manage plenty of services and perform day to day actions like stop, start and restart I think you would agree, If I say GUI is fun for entry-level but when it comes to...
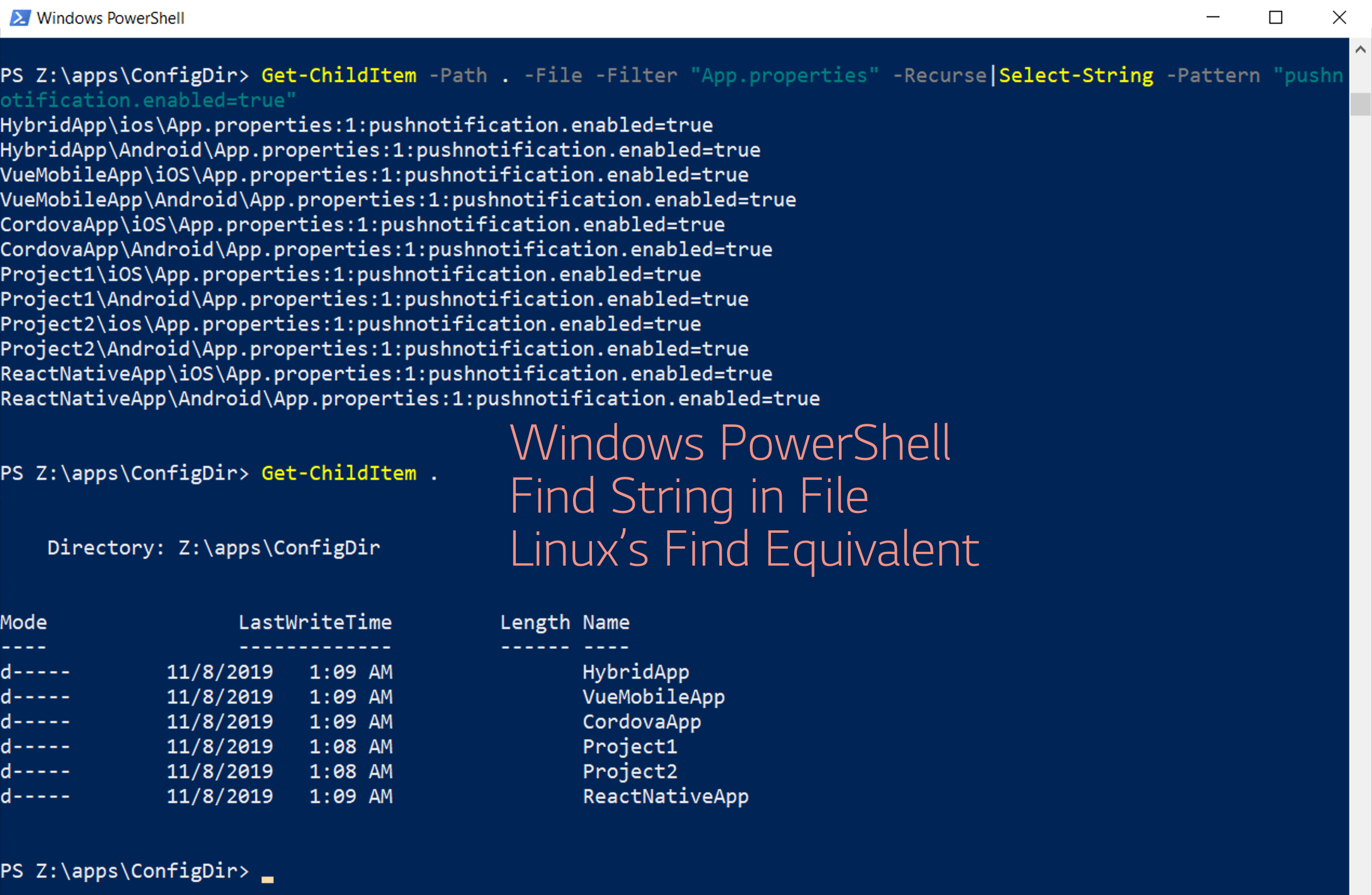
Powershell Find String in file - How to use windows find command
If you are here, Then you might have had a similar requirement I had, which is to find a specific file across multiple directories and to grep or Search for a string present in that file. ( more like what we do with xargs in Linux) I am a Linux user and If you would...
Ansible Shell Module Examples
Ansible shell module is designed to execute Shell commands against the target Unix based hosts. Unlike the Ansible command module, Ansible Shell would accept any highly complexed commands with pipes, redirection etc and you can also execute Shell scripts using...
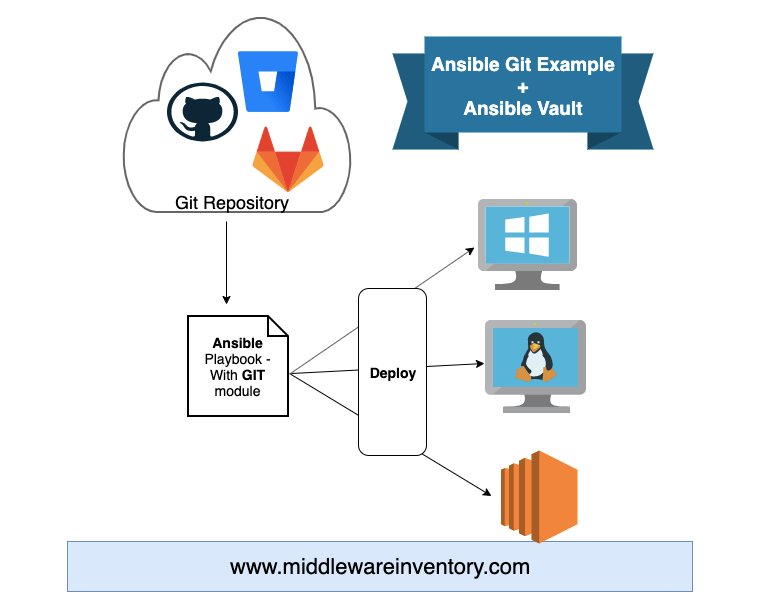
Ansible Git Example - Checkout code from Git Repo Securely
Introduction Ansible works seamlessly with Git and you might have had a requirement to download your source code or software directly from the Github, Bitbucket, Gitlab etc. In this post, we are going to explore various tits and bits of Ansible Git module and how to...
Netstat command windows - Usage and Examples
Introduction Like Linux, Windows does have a netstat command and it can come handy when you are in need of network-related monitoring and troubleshooting. Consider you have any of the following requirement How to find who or which process owns the port in Windows...
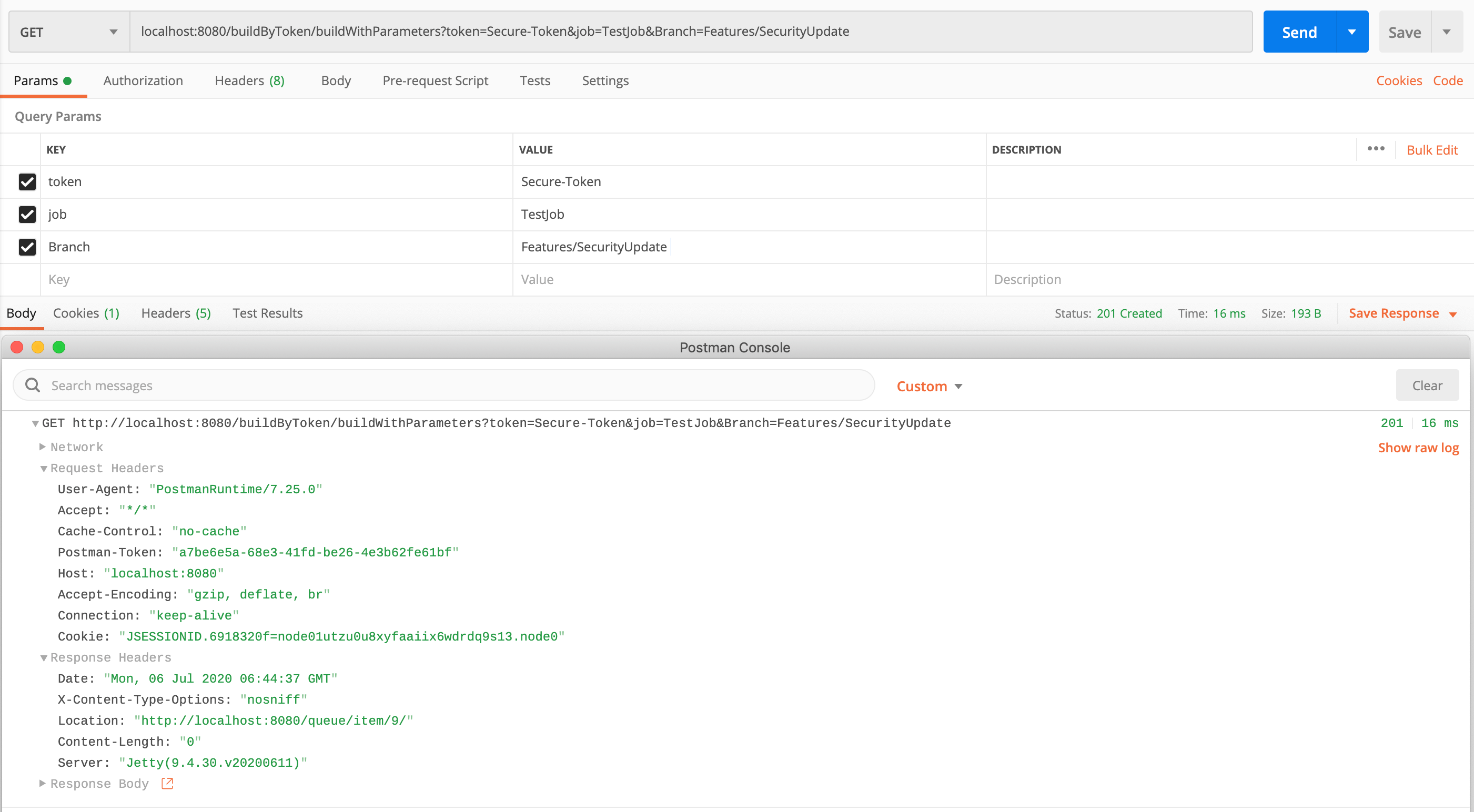
Jenkins Remote Build Trigger - Build Jobs with URL and Token
Jenkins Build Trigger using remote access API is a key element when it comes to automating the Deployment process and implementing the CI/CD pipelines with Jenkins. In this post, we are going to see how to create a Jenkins Job or Project and configure API token and...
Clickjacking attack - IIS
Overview Clickjacking (UI redress attack) is a malicious technique of tricking a user into clicking on something different from what the user perceives, thus potentially revealing confidential information or allowing others to take control of their...
Disabling IIS Web Banner And Other IIS Headers
Overview Microsoft IIS loves to tell the world that a website runs on IIS. It does so with the Serverheader in the HTTP response, as shown below. In this post I’ll show you how to remove response server headers in IIS. You don’t want to give hackers too...
WEBLOGIC Remote Code Execution CVE-2018-3191 - How to Fix
Overview Oracle Weblogic Remote Code Execution vulnerability allows unauthenticated attackers with network access via T3 to compromise vulnerable Oracle WebLogic Server. Successful exploitation of it can result in takeover of Oracle WebLogic Server, hence remote code...

ROBOT Return of Bleichenbacher Oracle Threat - How to Fix
Overview ROBOT is the return of a 19-year-old vulnerability that allows performing RSA decryption and signing operations with the private key of a TLS server. In 1998, Daniel Bleichenbacher discovered that the error messages given by SSL servers for errors in the PKCS...
Articles for DevOps Beginner
No Results Found
The page you requested could not be found. Try refining your search, or use the navigation above to locate the post.

