POODLE fix in Oracle weblogic server
Overview
Newer versions of web browsers (e.g. Chrome) are now configured with policies which only allow websites or portal which enforce the strongest encryption technology to be viewed. SSL version 3 is no more secure due to POODLE attack. Most of the browser disabled support for SSL Version 3 by default.
SSL version 3 is now vulnerable, Here you can go with strong ciphers to protect it ! ! !
Solution:
We need to disable SSL Version 3 and enable TLS protocol. We also need to enable strong ciphers. We can set either of the following system properties in the command-line argument that starts WebLogic Server
- weblogic.security.SSL.protocolVersion=TLS1
- weblogic.security.SSL.minimumProtocolVersion=TLS1
I would suggest to use 2nd option (depends on application security). This property value enables any protocol starting with "TLS" for messages that are sent and accepted; for example, TLS V1.0, TLS V1.1, and TLS V1.2.
Implementation in Weblogic Server
- Enable “Use JSSE SSL” option from WLS Console. For this purpsoe go to Servers> AdminServer or Managed Server >>Configuration>>SSL [Advance Tab]
- Now Shutdown domain
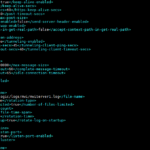
- Create a custom environment setting file “setCustomEnv.sh” with following lines:-
JAVA_OPTIONS="${JAVA_OPTIONS} -Dweblogic.security.SSL.minimumProtocolVersion=TLSv1.0"
export JAVA_OPTIONS
- Include setCustomEnv.sh file into $DOMAIN_HOME/bin/setDomainEnv.sh file:-
if [ "${WEBLOGIC_EXTENSION_DIRS}" != "" ] ; then
JAVA_OPTIONS="${JAVA_OPTIONS} -Dweblogic.ext.dirs=${WEBLOGIC_EXTENSION_DIRS}"
export JAVA_OPTIONS
fi
. ${DOMAIN_HOME}/bin/setCustomEnv.sh
JAVA_OPTIONS="${JAVA_OPTIONS}"
export JAVA_OPTIONS
- Add following lines in $DOMAIN_HOME/config/config.xml
<server>
<name>AdminServer</name>
<ssl>
<enabled>true</enabled>
<ciphersuite>TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA</ciphersuite>
<ciphersuite>TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA</ciphersuite>
<ciphersuite>TLS_ECDHE_RSA_WITH_3DES_EDE_CBC_SHA</ciphersuite>
<ciphersuite>TLS_RSA_WITH_AES_128_CBC_SHA</ciphersuite>
<ciphersuite>TLS_RSA_WITH_AES_256_CBC_SHA</ciphersuite>
<ciphersuite>TLS_RSA_WITH_3DES_EDE_CBC_SHA</ciphersuite>
<ciphersuite>TLS_RSA_WITH_AES_128_CBC_SHA256</ciphersuite>
<ciphersuite>TLS_RSA_WITH_AES_256_CBC_SHA256</ciphersuite>
<hostname-verifier xsi:nil="true"></hostname-verifier>
- In order to support strong ciphers (AES 256), we need to download install JCE package for JDK. Download the JCE package from the following location:
- Extract the downloaded zip and place the two .jar files US_export_policy.jar and local_policy.jar into your $JDK_HOME/jre/lib/security folder and overwrite old files.
- Start the domain
- Once server started, verify the site on different browser. I tested on Chrome version 45
10. Clear the cache of the SSL lab site and scan the website again.