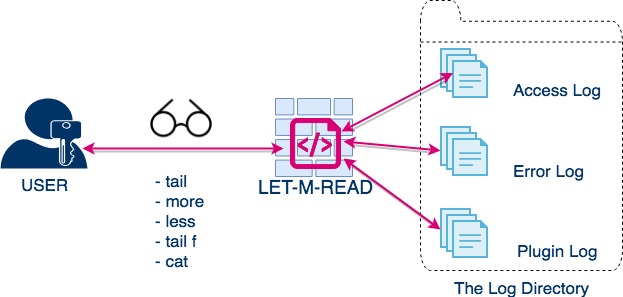
An Open Source tool to grant controlled read access to unprivileged users on UNIX based OS to read log files or config files etc. With LET-M-READ system admins can give read access to unprivileged or Guest users. without changing the file permissions (or) directory permissions.
LET-M-READ can help mostly while you want to give the Developers and Support teams a READ privilege to access the Apache, weblogic, WebSphere logs or any logs available in the server
- more
- tail
- tail with f
- less
- cat
You as System Admin would no longer have to change the file permission or directory permission to let the developers (or) support engineers access that log file or configuration file.
There by you are isolating and controlling who is reading the log file at what time etc.
Either Temporary or permanent. LET-M-READ will take care of it and logs what they are reading. Still everything is in your control.
Features
- User Authentication Enabled ( Maintains in own Secure file based User Database, SaltString used to encrypt and decrypt the passwords can be changed)
- Event Log capture on what the user has read
- Easy UserAddition
- User-Friendly
- Provides more options to unprivileged users for reading files
- Controlled Access
Prerequisites
- LET-M-READ should be stored and secured as root user to keep it fully functional and protected.
- Perl 5.10 or above must be present in the server with Switch module
- The commands being used by LET-M-READ less, more, tail, cat must be installed and have proper path precedence and defined in environment variable $PATH. As LET-M-READ will invoke the commands without path (not like
/usr/local/bin/moreit is just 'more')
Supported Operating System
The Scenario
How to Use?
- Download the Zip file from GITHUB & Uncompress it
- Add the User in LET-M-READ
- Update the Sudoers file
- Ask the user to test
If you are having GIT installed? Just do
git pull https://git.io/fxsBX
Download
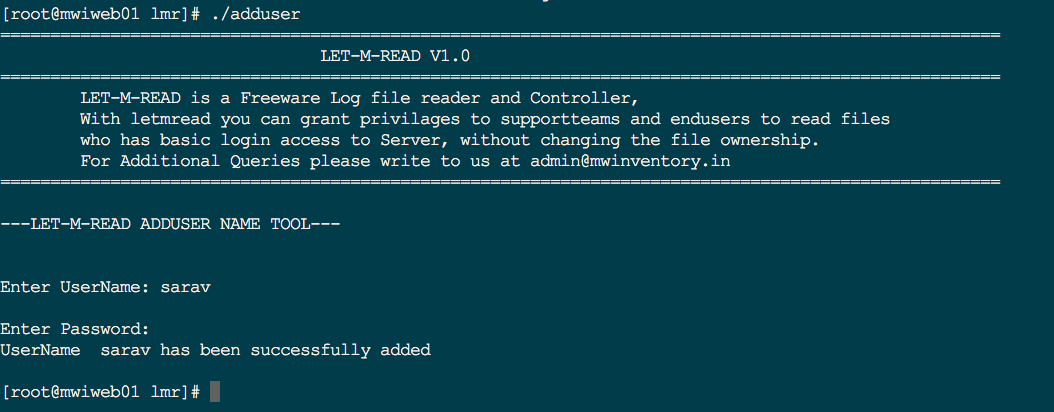
Step1: AddUser
./adduser
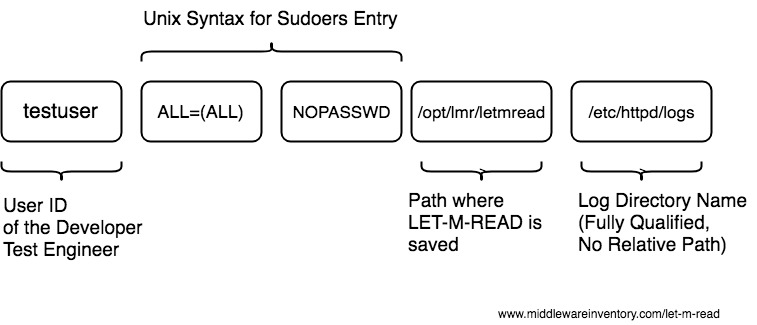
Step2: Update Sudoers File
id testuser
sudo visudo
testuser ALL=(ALL) NOPASSWD: /opt/lmr/letmread /etc/httpd/logs
/opt/lmr/letmread -> Fully qualified location where you have uncompressed and saved the letmread/etc/httpd/logs -> The Log Directory, for which you want to grant access to the 'testuser'
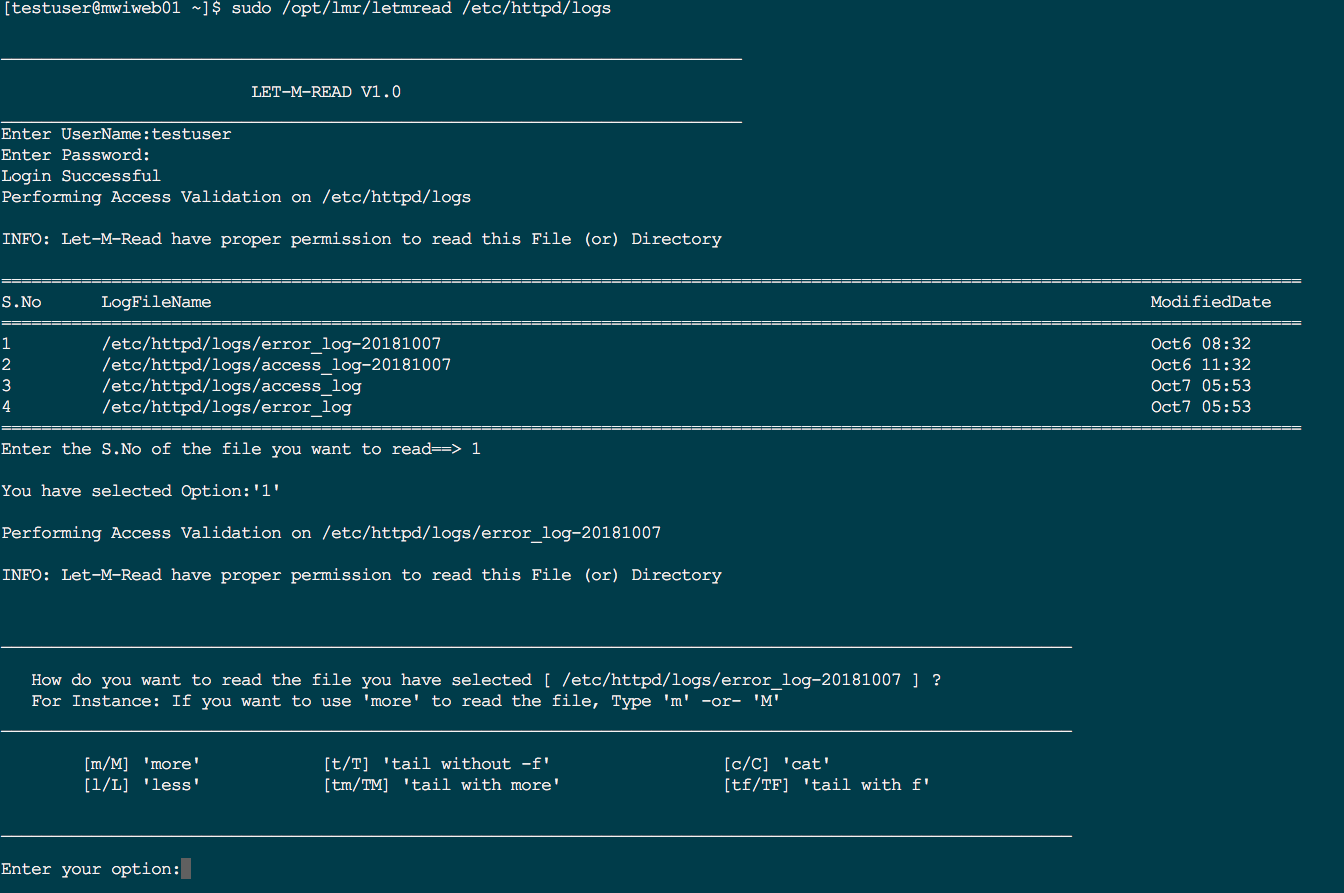
Testing: Invoking LET-M-READ (as testuser)
Now the user has to execute the following command ( the one we defined in sudoers)
sudo /opt/lmr/letmread /etc/httpd/logs
The Complete TrailRun (Setup & Testing)
Event Logging
[Oct 07 05:31:22:22] 'testuser' Reading '/etc/httpd/logs/access_log' with command 'm' [Oct 07 05:32:52:52] 'testuser' Reading '/etc/httpd/logs/access_log' with command 'l' [Oct 07 05:45:02:02] 'testuser' Reading '/etc/httpd/logs/access_log' with command 'm' [Oct 07 05:46:00:00] 'testuser' Reading '/etc/httpd/logs/access_log' with command 'l' [Oct 07 05:47:32:32] 'testuser' Reading '/etc/httpd/logs/access_log' with command 'tf'
The content of ZipFile.
adduser- this module can be used for adding new username into LET-M-READletmread- this is the core logic module and heart of LET-M-READlicense.txt- GPL V3 License Documentmore_instructions.txt- A supplementary text file being used by LET-M-READREADME.md- GIT repository Readme file.
Some screenshots:
Security - Changing the Salt String
As said earlier, LET-M-READ saves the username as encrypted text in a file named .pwfile and this file resides (or) gets created at the location where the letmread and adduser scripts are present in other words, the Base directory of LET-M-READ
For Encryption and Decryption we use a SHA256 SaltString which can be changed directly by editing the adduser and letmread scripts
In case you are changing the Salt String. You would have to recreate all the user names, already stored in the .pwfile
Disclaimer
This tool is created by me with no guarantee or warranty that it will work/satisfy all your needs and It is OpenSource. You can modify it edit to suit all your needs. You can first try it in your Development environments before going to production. user discretion is advised
FAQ:
1. What Guarantee does it provide that my log files are safe and it will not do any mess with my log file?
As tested by various users and by me for a long time, we never have seen that happening and LET-M-READ have never made any mess with the log file or left the log file in incompatible State. However user discretion is advised.
2. What Language this is developed in?
perl
3. Who is backing this tool (or) any commercial version available
I (SaravAK) Created this as my side project and It is Open Source
Hope it helps.
I would be happy to see your feedback through comments. Help LET-M-READ to improve by providing any suggestion/feedback.
If you find any bug/ want to suggest any moderation please use GitHub (or) comment here.
How would you like to rate this article and Tool [ratings]

Follow me on Linkedin My Profile Follow DevopsJunction onFacebook orTwitter For more practical videos and tutorials. Subscribe to our channel
Signup for Exclusive "Subscriber-only" Content