Overview Sweet32 affects TLS ciphers, also OpenSSL consider Triple DES cipher is now vulnerable as RC4 cipher . The DES ciphers (and triple-DES) only have a 64-bit block size. This enables an attacker to run JavaScript in a browser and send large amounts of traffic during the same TLS connection, creating[...]
Read moreAuthor: Sarav AK
Sweet 32 Attack - IHS
Overview Sweet32 affects TLS ciphers, also OpenSSL consider Triple DES cipher is now vulnerable as RC4 cipher . The DES ciphers (and triple-DES) only have a 64-bit block size. This enables an attacker to run JavaScript in a browser and send large amounts of traffic during the same TLS connection,[...]
Read moreDenial of Service or Slow Loris – Apache/IHS
Overview A Slowloris or Slow HTTP DoS attack is a type of denial of service that can affect thread-based web servers such as Apache. This means that your Apache web servers for Faspex or Console are vulnerable to this attack (applications based on nginx, such as Shares, are safe). The attack exploits[...]
Read more
How to enable SSH Key based authentication - Passwordless SSH
How to SSH without Password into remote Linux Server is the question that every Engineer working on Linux might have come across. Sometimes the Question we seek could be different like ssh command without password ssh to the remote server without password SSH without password from Shell Script SCP to[...]
Read more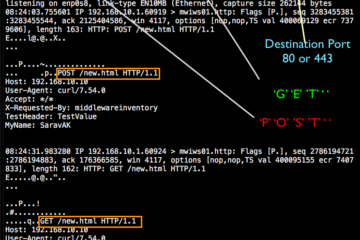
TCPDump Capture HTTP GET/POST requests
TCPDUMP is a swiss army knife for all the administrators and developers when it comes to troubleshooting. This post is written for the people who work in middleware technologies. Web servers such as Apache, NGINX, Oracle HTTP, IHS web servers and application servers such as Weblogic, Websphere, Tomcat, Jboss Consider[...]
Read moreArbitary File Download Vulnerability
Overview Some websites may provide file viewing or download functionality because of business needs. If you do not limit user from viewing or downloading files, a malicious user may attempt to view or download any file from your server. Attackers may construct malicious requests to download sensitive files from the[...]
Read moreOracle WebLogic Java Deserialization Vulnerability (CVE-2018-2628)
Overview Vulnerability in the Oracle WebLogic Server component of Oracle Fusion Middleware (subcomponent: WLS Core Components). Supported versions that are affected are 10.3.6.0, 12.1.3.0, 12.2.1.2 and 12.2.1.3. Easily exploitable vulnerability allows unauthenticated attacker with network access via T3 to compromise Oracle WebLogic Server via unsafe deserialization of Java objects. Successful[...]
Read moreHow to upgrade Java JDK version in Websphere 8.5
In this post we are going to see how to upgarde the websphere application server JDK from Java6 to 7.0 Download and install Java 7.0, which is shipped with Websphere application server v8.5.5 from Passport Advantage: Note: Java 7.0 fixpacks are shipped with every WAS v8.5.x fixpack, but base Java 7.0[...]
Read moreDisable WebServer Banner Apache/IHS
Overview Don’t display or send Apache version (Set ServerTokens) By default, the server HTTP response header will contains apache and php version. Something similar to the following. This is harmful, as we don’t want an attacker to know about the specific version number. Apache can reveal information by default configuration,[...]
Read moreWebserver Directory traversal
Webserver Directory traversal Overview File path traversal attack or directory traversal attack in web application is a common security issue.In this a hacker can get access to the files or directories of a webserver through the web url which will lead to major security issues. If you are using Apache[...]
Read more