Sarav is the creator and Founding Author of Devops Junction. He has 13+ years of experience in Software Development and Architecture. He has written around 250+ articles on various technologies.
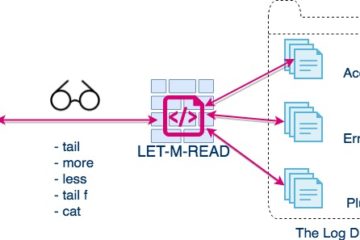
An Open Source tool to grant controlled read access to unprivileged users on UNIX based OS to read log files or config files etc. With LET-M-READ system admins can give read access to unprivileged or Guest users. without changing the file permissions (or) directory permissions. LET-M-READ can help mostly while[...]
Read more

In this post, we are going to see how to use conditional statements of Ansible such as when, changed_when, failed_when and where to use them appropriately and how it works. By these conditional modules, Ansible provides a way for us to define when should ansible run a certain task or consider the[...]
Read more
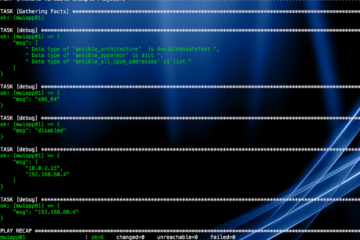
In this post, we are going to see, What is ansible facts (or) playbook variables and how to use these facts various types of facts such as Dictionary, List, Normal Text. Also covered, What does ansible Gathering facts tasks do in ansible playbook execution, data types of ansible variables and how[...]
Read more
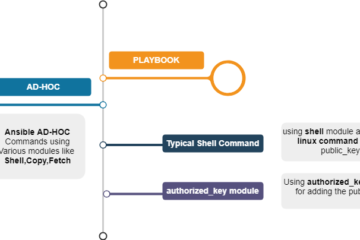
SSH Key-based authentication setup in LINUX (or) UNIX based OS is one of the major platform services related task and most frequently executed task by Unix admins. Ansible, An IT Automation tool could automate this tedious task as well. SSH Key based authentication is indispensable when it comes to automation. Even[...]
Read more
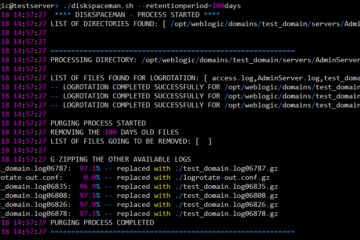
Overview An Automation script Linux for Log rotation, LogPurging and Compressing For weblogic and tomcat Installations. In Big infrastructure when you are running multiple Tomcat, weblogic, JBoss (or) Websphere instances or domains. The Biggest problem that you would face often as a system administrator is disk space issue. Perhaps, the[...]
Read more
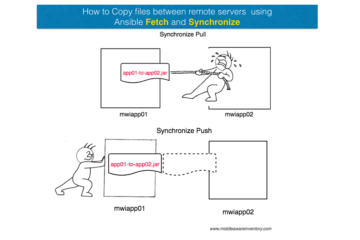
How to copy files between remote servers in Ansible ?. is the purpose behind this article. Every article I went and read was giving me suggestions but nothing practical. I simply wanted to do make ansible rsync. I wanted to execute rsync between remote hosts and copy files between remote[...]
Read more
In this post, we are going to briefly cover, What is web services and its types? How to develop a Simple SOAP Web service for Weblogic? followed by deployment and testing using POSTMAN and SOAP UI We use Weblogic 12c application server as a platform to deploy our Simple SOAP[...]
Read more

Overview SSL Cipher is an encryption algorithm, which is used as a key between two computers over the Internet. Data encryption is the process of converting plain text into secret ciphered codes. It’s based on your web server SSL Cipher configuration and strong protocol that allows data encryption to take[...]
Read more
Overview Sweet32 affects TLS ciphers, also OpenSSL consider Triple DES cipher is now vulnerable as RC4 cipher . The DES ciphers (and triple-DES) only have a 64-bit block size. This enables an attacker to run JavaScript in a browser and send large amounts of traffic during the same TLS connection, creating[...]
Read more
Overview Cross Site Scripting (XSS) protection can be bypassed in many browsers. You can apply this protection for a web application if it was disabled by the user. This is used by a majority of giant web companies like Facebook, Twitter, Google, etc. Solution Go to $Web_Server/conf directory Open[...]
Read more








