Sarav is the creator and Founding Author of Devops Junction. He has 13+ years of experience in Software Development and Architecture. He has written around 250+ articles on various technologies.

Some Background When it comes to handling the web application related vulnerabilities. Most of the vulnerabilities could be fixed by having the proper configuration at the F5 level. By using the right configuration at the F5. like having proper SSL Cipher at the SSL profile of the VIP (or) creating and[...]
Read more
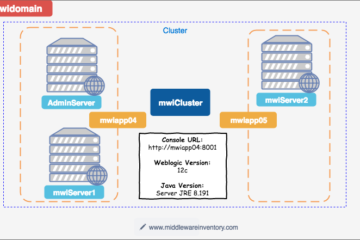
The Objective We are going to create an Ansible role (or) playbook to quickly build a distributed, multi-node, Fully featured Weblogic Domain with two managed servers and a horizontal cluster and machines In a single line, Ansible role to build, Weblogic Infrastructure with Managed Server, Admin Server and a Cluster on[...]
Read more

The Purpose The purpose of this post is to give you a real-time example and explanation of how ansible variable is defined and not defined (undefined) conditionals are working along with "when" conditional statement and how it controls the flow of the task and the play. The following ansible playbook is[...]
Read more

The Introduction to Docker Weblogic In this post, we are going to be exploring the quick and easy option available to get started with weblogic and Docker. In this post, we are going to see how to create a weblogic container in docker in a few easy steps. The post's[...]
Read more

Some Background Weblogic distribution is the terminology that depicts the form or the nature of the Oracle Weblogic Installer (or) the installable files. Oracle weblogic 12c can be downloaded in two forms. Generic Distribution Developer Distribution What is Generic Distribution In Generic Distribution, Oracle has bundled the Weblogic server and[...]
Read more
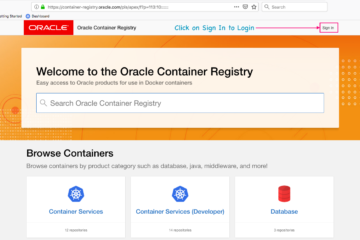
In this article we are going to see how to fix the access denied and unauthorized errors while using the containers of container-registry.oracle.com. Most of us at times might have got this exceptions access denied and unauthorized while downloading the image using docker pull command. This article is all about[...]
Read more

In this post, we are going to see the Steps to create a Docker Image and Deploy to Kubernetes in 8 easy steps. This post is about the title of this post which is "How to Deploy docker image to kubernetes" For this post, we have used minikube cluster and[...]
Read more
The Objective Let it be any Application Server you use such as Weblogic, Websphere, Tomcat, Jboss, Glassfish. (or) Let it be any Java framework or architecture your web application is developed in like Spring MVC, EJB, JSF, DAO. When it comes to administrating the Java (J2EE) application ( WEB or[...]
Read more
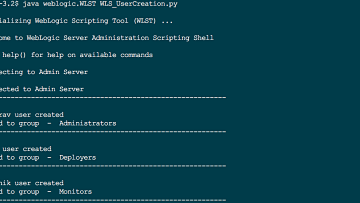
The Objective The purpose of this post to share the WLST script which helps in creating a new user in weblogic 11g or 12c and map them to righteous Group for privileges. Like Administrators, Deployers, Monitors etc. Version Compatibility Weblogic 12c (or) 11g The Properties file This is[...]
Read more
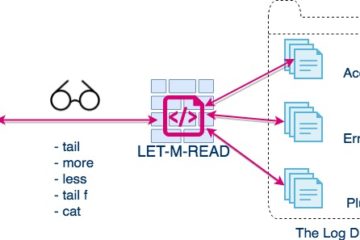
An Open Source tool to grant controlled read access to unprivileged users on UNIX based OS to read log files or config files etc. With LET-M-READ system admins can give read access to unprivileged or Guest users. without changing the file permissions (or) directory permissions. LET-M-READ can help mostly while[...]
Read more










