Sarav is the creator and Founding Author of Devops Junction. He has 13+ years of experience in Software Development and Architecture. He has written around 250+ articles on various technologies.
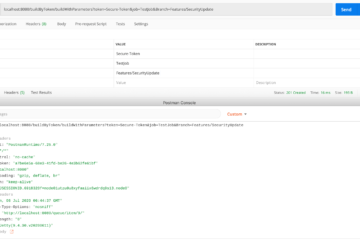
Jenkins Build Trigger using remote access API is a key element when it comes to automating the Deployment process and implementing the CI/CD pipelines with Jenkins. In this post, we are going to see how to create a Jenkins Job or Project and configure API token and enable REMOTE API[...]
Read more
Overview Clickjacking (UI redress attack) is a malicious technique of tricking a user into clicking on something different from what the user perceives, thus potentially revealing confidential information or allowing others to take control of their computer while clicking on seemingly innocuous objects, including web pages. Affected versions IIS 7.x IIS 8.x Solution [...]
Read more
Overview Microsoft IIS loves to tell the world that a website runs on IIS. It does so with the Serverheader in the HTTP response, as shown below. In this post I’ll show you how to remove response server headers in IIS. You don’t want to give hackers too much information[...]
Read more
Overview Oracle Weblogic Remote Code Execution vulnerability allows unauthenticated attackers with network access via T3 to compromise vulnerable Oracle WebLogic Server. Successful exploitation of it can result in takeover of Oracle WebLogic Server, hence remote code execution Affected versions Weblogic 10.3.6.0 Weblogic 12.1.3.0 Weblogic 12.2.1.3 Solution This vulnerability[...]
Read more

Overview ROBOT is the return of a 19-year-old vulnerability that allows performing RSA decryption and signing operations with the private key of a TLS server. In 1998, Daniel Bleichenbacher discovered that the error messages given by SSL servers for errors in the PKCS #1 v1.5 padding allowed an adaptive-chosen ciphertext[...]
Read more
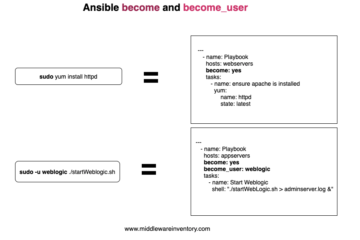
Ansible Sudo or Ansible become Introduction Ansible Sudo or become is a method to run a particular task in a playbook with Special Privileges like root user or some other user. In the earlier versions of ansible there is an option named as sudo which is deprecated now, Since ansible[...]
Read more

Overview Oracle WebLogic is vulnerable to a new deserialization vulnerability that could allow an attacker to execute remote commands on vulnerable hosts. This vulnerability was identified in China by China National Vulnerability Database (CNVD) published a Security Team, they have issued a bulletin about an unauthenticated remote command execution (RCE)[...]
Read more
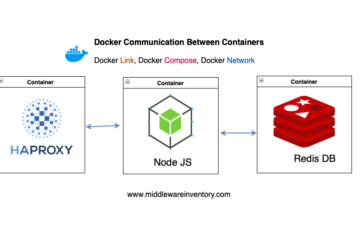
In this post we are going to see How to establish docker network between containers, How to Link Docker Containers, How to Access one Container from Another, Docker inter-container communication, How to Connect to Container, etc. This post is to answer all that. So How do we connect a[...]
Read more

Ansible Dry Run or Ansible Check mode feature is to validate your playbook before execution With the Ansible Dry Run feature, you can execute the playbook without having to actually make changes on the server. this enables us to see what changes are going to be made when the playbook[...]
Read more

In this post, we are going to see examples of Ansible playbook and various different modules and playbook examples with various modules and multiple hosts. We will start with a basic Ansible playbook and learn what is task and play and what is playbook etc. What is Ansible Playbook It[...]
Read more






