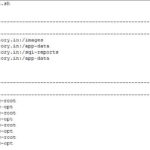
Overview
Some websites may provide file viewing or download functionality because of business needs. If you do not limit user from viewing or downloading files, a malicious user may attempt to view or download any file from your server.
Attackers may construct malicious requests to download sensitive files from the server, and further embed website webshell files to control the website server host.
Solution
Please remove Indexes to stop Directory listing and this will also prevent Arbitrary file download vulnerability, below are steps to configure the same in Apache configuration file httpd.conf.
Update the below configurations any where in the httpd.conf file
</VirtualHost>
<Directory "/var/www/html/ncn">
Options Indexes FollowSymLinks MultiViews
AllowOverride None
Order allow,deny
Allow from 127.0.0.1
Deny from all
</Directory>
</VirtualHost>
Additional you can configure which and what types of files can be secured from arbitrary download.
<Directory /var/www/example/subdomains/dev/public/webapp>
RewriteEngine Off
<Files *>
order allow,deny
deny from all
</Files>
<FilesMatch "\.(png|gif|jpe?g|png|css|js|swf|ps|flv)$">
order allow,deny
allow from all
</FilesMatch>
</Directory>
– Restart the apache services and test the weburl.
More from Middleware Inventory
-
Ansible get_url Examples - How to download file from URLIn this post, we are going to see how to download a file from URL using ansible get_url module in other words ansible curl. As we know it already, Ansible has a lot of built-in modules to accomplish all the tasks we might need for configuration management and automation. Ansible…
-
-
Remote Server - File System Lister [Linux]Have you ever had the requirement of logging in to the Nnumber of remote servers (without keybased authentication ) and get the mount point information and save it as CSV Report (or) Print it with a good console formatting. Then this is for you. Basically, It is a Shell script (…
Oracle WebLogic Java Deserialization Vulnerability (CVE-2018-2628) Overview Vulnerability in the Oracle WebLogic Server component of Oracle Fusion Middleware (subcomponent: WLS Core Components). Supported versions that are affected are 10.3.6.0, 12.1.3.0, 12.2.1.2 and 12.2.1.3. Easily exploitable vulnerability allows unauthenticated attacker with network access via T3 to compromise Oracle WebLogic Server via unsafe deserialization of Java objects. Successful…
Webserver Directory traversalWebserver Directory traversal Overview File path traversal attack or directory traversal attack in web application is a common security issue.In this a hacker can get access to the files or directories of a webserver through the web url which will lead to major security issues. If you are using Apache…