In this article, We are going to discuss how to encrypt the Tomcat DataSource Password and avoid clear text password in Context.xml.
If you are using Tomcat Application server's Datasource Feature, You must be aware that there is a Security issue as the DataSource or Database Connection Password would be in the Clear Text format on the context.xml file
Whoever get access to the context.xml file Or the Server where the tomcat instance is hosted, Can take the Connection Details like JDBC username, JDBC password including the remote the Database Server and Schema Information.
Having, The Username and Connection details as a clear text is OK to some extent but Having the Password Unencrypted or as clear text is really a big Loophole you are leaving for your own Infrastructure Destruction. It is one of the Critical Security Vulnerability.
A Quick Fix (or) A Workaround
These are the list of Steps you can do at an instant basis to Secure your Context.xml and DataSource Password.
- Make sure you restrict the file permission of the context.xml (or) all the configuration files associated with tomcat under the
$CATALINA_HOME/conf/*by restricting access to the Group and others. It can be done easily with the chmod command in linuxchmod 600 context.xml - Setup ACL (Access Control List) for that file and Directory, With the help of
setfaclandgetfaclcommands in Linux - Have Auditing on who is viewing the file or copying the file
- Control who know the password of tomcat user (or) who have SUDO privileges and make sure they are the best people to hold the fort.
Despite doing everything, All these workarounds, Your System is still prone to RISK as long as someone can read the password as Clear Text.
The Recommended and Reasonable approach is to have the password Encrypted.
How to Encrypt Tomcat DataSource Password
By Default, the Password in Context.xml is not encrypted and Tomcat does not take that responsibility unlike the other application servers in the market like Weblogic and Websphere.
So we are left out with only one option which is to write our own Encryption and Decryption Mechanism and a DataSource Implementation.
Don't panic. We have a Solution.
Protect your JDBC Tomcat Passwords with SecureTomcatJDBC
We have created a small application with Shell Script and Java and named this project as SecureTomcatJDBC
This works as an Encryptor and Decryptor of the Password using the Passphrase provided in an AES Algorithm and also act as a DataSource Connection Factory Implementor to Create JDBC Connections using the Encrypted passwords which can be used by the application as usual.
There are two Java files used and they are EncDecJDBCPass.java and SecureTomcatDataSourceImpl.java
HereSecureTomcatDataSourceImpl.java is a Customized DataSource Connection factory Code which is going to be used in the context.xml to create the DB Connections for the Applications and on the other handEncDecJDBCPass.java is just an Encryptor and Decryptor Class.
In fact, This DataSource Class SecureTomcatDataSourceImpl.java replaces the regular org.apache.tomcat.jdbc.pool.DataSourceFactory in context.xml .
What is Secure Tomcat JDBC in 10 Crisp Points
- A Solution to use Encrypted Password in tomcat JDBC
- An extension of traditional
org.apache.tomcat.jdbc.pool.DataSourceFactory - Uses AES Algorithm to Encrypt and Decrypt Password
- It is a Connection Factory alternative to
org.apache.tomcat.jdbc.pool.DataSourceFactory - All the configuration parameters can be used as usual
- Built with Shell Script and Java files
- Works with Tomcat7 and Tomcat8 and May not be applicable for Tomcat6 as it uses dbcp pool configuration
- Leave No Foot Print of SecurityKey or Password anywhere on the filesystem
- Enable Additional Logging, and log useful information like ConnectionURL and username upon successful ConnectionPool Creation. Helpful to troubleshoot
- Completely Open Source - Can be tweaked to suit your needs
So what is the Difference between The Regular DataSource and SecureTomcatJDBC
As mentioned earlier there is no Major Difference in terms of Creating and managing the Connections to the DB as the Regular and SecureTomcatJDBC both uses org.apache.tomcat.jdbc.pool.DataSourceFactory
SecureTomcatJDBC just adds an additional layer of Security Encryption and Decryption that's all
Since we are going to use SecureTomcatJDBC to create connections for us. we need to update the factory
in the context.xml. That's All.
In Regular Context.xml
<Resource name="jdbc/TestDB"
auth="Container"
type="javax.sql.DataSource"
factory="org.apache.tomcat.jdbc.pool.DataSourceFactory"
testWhileIdle="true"
testOnBorrow="true"
testOnReturn="false"
password="s3cuR3"
........
........
With SecureTomcatJDBC in Context.xml
<Resource name="jdbc/TestDB"
auth="Container"
type="javax.sql.DataSource"
factory="SecureTomcatDataSourceImpl"
testWhileIdle="true"
testOnBorrow="true"
testOnReturn="false"
password="5d89fde03skdkd024oxipasdfiekflzwe9"
........
........
How to use this?
- Download the Zip distribution of SecureTomcatJDBC
- UnCompress/Unzip to any Directory
- Start the Script
SecureTomcatJDBC.sh - Enter the
CATALINA_HOMEdirectory as an Input and JAVA_HOME and All other Required Parameters will be auto fetched - Enter the Password to Encrypt including the Pass Phrase
- Copy the Generated
SecureTomcatJDBC.jarinto the$CATALINA_HOME/libdirectory - Replace the Factory element in Context.xml with
factory=“SecureTomcatDataSourceImpl” - Replace the Encrypted Password in place of Clear Text Password
password="ENCRYPTED PASSWORD”
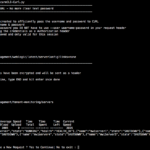
Here is a Sample Execution output.
[tomcat@mwivmapp02 SecureTomcatJDBC]$ ./SecureTomcatJDBC.sh
Enter the Tomcat Instance CATALINA_HOME ( A Parent Directory of conf/ bin/ webapps/ )
/apps/tomcat/tomcat7
Server version: Apache Tomcat/7.0.93
JVM Version: 1.7.0_80-b15
Using JRE_HOME: /apps/tomcat/jdk1.7.0_80
Using CATALINA_HOME: /apps/tomcat/tomcat7
Using CLASSPATH: /apps/tomcat/tomcat7/bin/bootstrap.jar:/apps/tomcat/tomcat7/bin/tomcat-juli.jar
INFO: Java Home Validation Successful. Good to Go
INFO: Vaidating the Tomcat Juli and Tomcat JDBC Jar files availability
INFO: Jar files are present. Good to Go
Enter the Password to Encrypt
Enter the Secret PassPhrase
Creating the JAR module and Compiling the code
Class files are created. Good to Go
INFO: Creating a Jar file SecureTomcatJDBC.jar
adding: EncDecJDBCPass.class(in = 3210) (out= 1773)(deflated 44%)
adding: SecureTomcatDataSourceImpl.class(in = 2975) (out= 1463)(deflated 50%)
adding: META-INF/(in = 0) (out= 0)(stored 0%)
adding: META-INF/MANIFEST.MF(in = 49) (out= 49)(deflated 0%)
INFO: Jar file Creation Successful. Good to Go
Password Encryption Begins
=> ENCRYPTED PASSWORD : e590bacfa29f5f774365a665d35d2dd0
Password Encryption Completed. Your Encrypted Password is displayed above
Next Steps:
1) Copy the Generated SecureTomcatJDBC.jar into the /apps/tomcat/tomcat7/lib directory
2) Replace the Factory element in Context.xml with factory="SecureTomcatDataSourceImpl"
3) Replace the Encrypted Password in place of Clear Text Password password="ENCRYPTED PASSWORD"
For Any Questions about this tool read the product page https://www.middlewareinventory.com/blog/secure-tomcat-jdbc/. Leave a Comment there for any help
Good Bye. Thanks for using SecureTomcatJDBC Application
After Executing and Encrypting your password you need to perform the following Three steps as shown in the preceding Sample Execution output
- Copy the Generated SecureTomcatJDBC.jar into the
$CATALINA_HOME/libdirectory - Replace the Factory element in Context.xml with
factory="SecureTomcatDataSourceImpl" - Replace the Encrypted Password in place of Clear Text Password
password="ENCRYPTED PASSWORD"
The Sample Context.xml with SecureTomcatDataSourceImpl Factory
Here is the Context.xml file sample with SecureTomcatDataSourceImpl Class and The Encrypted Password.
<?xml version="1.0" encoding="UTF-8"?>
<!--
Licensed to the Apache Software Foundation (ASF) under one or more
contributor license agreements. See the NOTICE file distributed with
this work for additional information regarding copyright ownership.
The ASF licenses this file to You under the Apache License, Version 2.0
(the "License"); you may not use this file except in compliance with
the License. You may obtain a copy of the License at
http://www.apache.org/licenses/LICENSE-2.0
Unless required by applicable law or agreed to in writing, software
distributed under the License is distributed on an "AS IS" BASIS,
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
See the License for the specific language governing permissions and
limitations under the License.
-->
<! – The contents of this file will be loaded for each web application – >
<Context>
<! – Default set of monitored resources. If one of these changes, the – >
<! – web application will be reloaded. – >
<WatchedResource>WEB-INF/web.xml</WatchedResource>
<WatchedResource>${catalina.base}/conf/web.xml</WatchedResource>
<! – Uncomment this to disable session persistence across Tomcat restarts – >
<!--
<Manager pathname="" />
– >
<Resource name="jdbc/mysqldb"
factory="SecureTomcatDataSourceImpl"
auth="Container"
type="javax.sql.DataSource"
maxActive="30"
minIdle="10"
maxWait="10000"
username="tomcat7usr"
initialSize="10"
removeAbandonedTimeout="60"
removeAbandoned="true"
password="e590bacfa29f5f774365a665d35d2dd0"
driverClassName="com.mysql.jdbc.Driver"
url="jdbc:mysql://192.168.43.42:3306/mysql?zeroDateTimeBehavior=convertToNull" />
</Context>
In the file, The factory and password elements are highlighted in Yellow colour. Rest of the configuration elements would be as same as the Traditional org.apache.tomcat.jdbc.pool.DataSourceFactory configuration.
After performing all these steps It is necessary you need to restart the Subjected Tomcat Instance for the changes to take effect.
How to Make Sure the New DataSource is working or docked properly?
Make sure there is no NO CLASS DEF found errors or any other Major Errors found in the Catalina.out file. If everything is all right, you would be able to see the Something Similiar to this
INFO: Creating a New Connection Pool for DataSource {name=} with URL
jdbc:mysql://192.168.43.42:3306/mysql?zeroDateTimeBehavior=convertToNull and the
username tomcat7usr
Is not it Good?. You can see What Connection Pool Getting created with the JDBC Connection URL and the username.
WhileTroubleshooting an issue where your application is not working properly. Now you can easily eliminate the DataSource as the cause or Go straight to it. I have added this cause I have had issues where DB was the cause and I could not find any log written in
Catalina.out
SecureTomcatJDBC in Action - Video Guide
GitHub Page of this Tool: https://github.com/AKSarav/SecureTomcatJDBC
The Sample DBApp used in this post is also available in the Github page including the Source codes.
Hope this tool is helpful to you.
If you like this, please spread the word and share this post
Rate this tool and article [ratings] and feel free to comment for any help and queries
Cheers
Sarav AK

Follow me on Linkedin My Profile Follow DevopsJunction onFacebook orTwitter For more practical videos and tutorials. Subscribe to our channel
Signup for Exclusive "Subscriber-only" Content